Here are some commonly asked interview questions and answers related to Microsoft Defender:
What is Microsoft Defender and how does it work?
Microsoft Defender is a security solution offered by Microsoft for protecting endpoints, servers, and cloud services against a variety of threats, including malware, phishing, and other attacks. It works by using a combination of machine learning, behavioural analysis, and signature-based detection to identify and remediate threats.
How do you configure Microsoft Defender?
Microsoft Defender can be configured through the Microsoft Defender Security Center portal, which provides a single interface for managing and monitoring security across all endpoints and servers. Configuration options include defining security policies, managing updates and patches, configuring threat detection settings, and setting up automated responses to security incidents.
What is Microsoft Defender ATP?
Microsoft Defender ATP (Advanced Threat Protection) is an enhanced version of Microsoft Defender that provides additional security features, such as endpoint detection and response (EDR), automated investigation and response, and integration with other security tools.
How does Microsoft Defender detect and respond to threats?
Microsoft Defender uses a variety of techniques to detect and respond to threats, including behavioural analysis, machine learning, and signature-based detection. When a threat is detected, Microsoft Defender can take automated actions to contain and remediate the threat, such as quarantining affected files, blocking network access, or deleting malicious files or registry keys.
What is the role of the Microsoft Defender Security Operations Center (SOC)?
The Microsoft Defender SOC is a team of security experts who monitor and respond to security incidents detected by Microsoft Defender. The SOC uses a combination of automated tools and human expertise to investigate and remediate security incidents and works closely with other security teams and law enforcement agencies to prevent and mitigate cyber-attacks.
How do you troubleshoot issues with Microsoft Defender?
To troubleshoot issues with Microsoft Defender, you can review the logs and diagnostic data provided by the software, as well as the logs of any other security tools that may be integrated with Microsoft Defender. You can also contact Microsoft support or consult online resources and user forums to find solutions to common issues.
What is your experience working with Microsoft Defender?
Be prepared to discuss your experience with Microsoft Defender, including any previous roles where you have managed or configured the software, your understanding of its features and capabilities, and any specific examples of how you have used it to detect and respond to security threats.
How does Microsoft Defender integrate with other security tools?
Microsoft Defender can integrate with other security tools through APIs and connectors, allowing it to share threat intelligence and coordinate responses to security incidents. Some examples of tools that Microsoft Defender can integrate with include SIEM (security information and event management) systems, threat intelligence platforms, and endpoint detection and response (EDR) solutions.
What are some common types of threats that Microsoft Defender can detect and mitigate?
Microsoft Defender is designed to protect against a wide range of threats, including viruses, malware, spyware, ransomware, phishing attacks, and other types of cyber threats. It can also detect and remediate vulnerabilities and security weaknesses in systems and applications.
How does Microsoft Defender protect against zero-day attacks?
Microsoft Defender uses a variety of advanced threat detection techniques, such as behavioural analysis and machine learning, to identify and respond to previously unknown or zero-day attacks. It also leverages threat intelligence data from the Microsoft Intelligent Security Graph, which uses machine learning and AI to analyze billions of signals from across the Microsoft ecosystem.
What is the process for updating and patching Microsoft Defender?
Microsoft Defender receives regular updates and patches through Windows Update, and these can also be managed through the Microsoft Defender Security Center portal. Updates may include new threat definitions, software enhancements, and bug fixes.
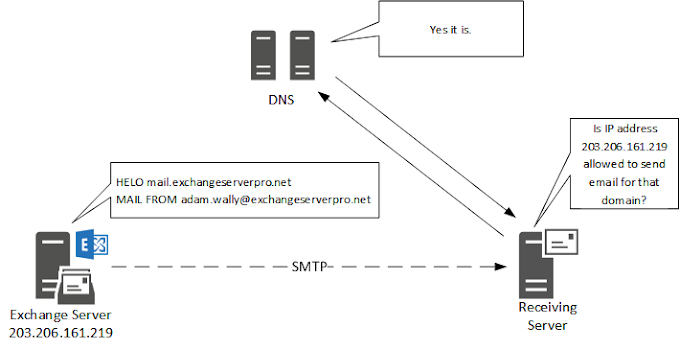
How does Microsoft Defender protect against phishing attacks?
Microsoft Defender uses a variety of techniques to protect against phishing attacks, including email filtering and link scanning, reputation analysis of sender domains and IPs, and analysis of message content and attachments for known phishing indicators. It also provides user education and awareness training to help users identify and report potential phishing emails.
What are some best practices for configuring and managing Microsoft Defender?
Some best practices for configuring and managing Microsoft Defender include regularly reviewing and updating security policies, configuring automated threat response actions, monitoring and analyzing security logs and alerts, and ensuring that all systems and applications are regularly patched and updated. It is also important to provide ongoing user education and awareness training to help prevent human error and reduce the risk of security incidents.
What are some common challenges faced when using Microsoft Defender?
Common challenges when using Microsoft Defender may include false positives or false negatives in threat detection, configuration and policy management complexity, issues with compatibility with other security tools or applications, and difficulty managing security across a large number of endpoints or servers.
How does Microsoft Defender integrate with Microsoft 365 and Azure?
Microsoft Defender integrates with Microsoft 365 and Azure through a variety of connectors and APIs, allowing it to share threat intelligence and coordinate responses to security incidents. For example, Microsoft Defender can be integrated with Microsoft Cloud App Security to provide additional visibility and control over cloud applications and services.
What are some benefits of using Microsoft Defender?
Some benefits of using Microsoft Defender include centralized security management and monitoring, advanced threat detection and response capabilities, integration with other security tools and services, and regular updates and patches for ongoing protection against new and emerging threats.
How does Microsoft Defender protect against ransomware attacks?
Microsoft Defender uses a multi-layered approach to protect against ransomware attacks, including behavioural analysis and machine learning to identify ransomware behaviour, anti-tampering and anti-exploitation technologies to prevent ransomware from evading detection, and built-in backup and recovery options to help restore data in the event of a ransomware attack.
How does Microsoft Defender protect against fileless attacks?
Microsoft Defender uses a variety of techniques to protect against fileless attacks, including behavioural analysis and machine learning to identify malicious behaviour, memory scanning and process injection detection to detect attacks that do not involve files, and integration with other security tools such as Windows Defender Application Control to prevent untrusted code from running.
How does Microsoft Defender integrate with Windows Virtual Desktop?
Microsoft Defender can be configured to provide protection for Windows Virtual Desktop environments, including virtual machines and applications. This can be achieved through the use of specialized security extensions and APIs that allow for centralized security management and monitoring across virtualized environments.
How does Microsoft Defender protect against supply chain attacks?
Microsoft Defender uses a variety of techniques to protect against supply chain attacks, including reputation analysis of software publishers and distributors, vulnerability detection and patch management, and integration with other security tools and services to identify and respond to potential threats at every stage of the software supply chain.
How does Microsoft Defender protect against credential theft?



.png)






0 Comments